PROTECT YOURSELF FROM ONLINE ROMANCE SCAMMERS
Enhance your online dating savvy by familiarizing yourself with scammers' tactics.
Draw wisdom from real-life examples and fortify your defenses against malicious individuals.
Stay informed and safeguard your online interactions effectively.

Romance Scammers' Favorite Lies Exposed
Romance scammers tell all sorts of lies to steal your heart and money, and reports to the FTC show those lies are working.
Last year’s romance scam numbers looked a lot like 2021 all over again, and it’s not a pretty picture.
In 2022, nearly 70,000 people reported a romance scam, and reported losses hit a staggering $1.3 billion.
The median reported loss: $4,400.
Data Spotlight from https://www.ftc.gov/
Consumer Affairs SilverSingles Reviews
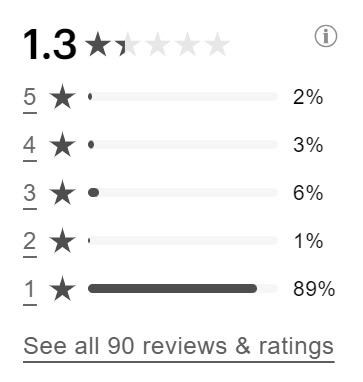
(https://www.consumeraffairs.com/dating_services/silversingles.html):
"Back away. Worst money I've ever spent. Nothing but scammers..."
"It's all full of scammers and false profiles..."
"Just horrible. Full of scammers..."
"This site is now taken over by scammers. Your inbox will quickly fill-up by scam messages..."
"Silver Singles is a total waste of time and money. The only activity you'll have is deleting messages from scammers..."
"I've collected over 50 emails from Silver Singles saying they value my security. Yet, the fakers are prolific...
And so on...
Let's start with two examples I looked into to give you some clues.

"… a little more about myself... … I live alone with my dog and his name is Terry …. I will show you my website so you can check and know more about my archaeology job....."
Attention!
Before checking links you received, ensure your browser and security software are updated with the latest patches.
Check the tools you can use to ensure it is safe to click on them.
Let's check the site registration.
Domain Registered: 2023-08-14
Domain Expires: 2024-08-14
1 year registration
Short domain registration periods should raise suspicions, as they are often associated with temporary or less trustworthy sites.
I used https://validator.schema.org to view the HTML source of the site without being exposed to viruses.
The information I've acquired might sound like a trick to the average user, but it's not. If you're interested in delving deeper, it's worth investigating further.
From the meta-tag descriptions I've read:
"Private ... Archaeologist is a licensed firm that extends its services across the globe, spanning North America, South America, Europe, Asia, and Africa."
However, there's no mention of the license on the site, and the company isn't listed in the Register of Professional Archaeologists.
Digging further into the Spammer#1 site's source...
Spammer#1 site's blog:
Interesting reading, but it is trivial to find the source from which the descriptions have been simply stolen. Just googling will help.
Caesar’s Forum - The description has been simply copied from:
The Great Maya Aquifer - The description has been simply copied from:
Last Supper in Pompeii - The description has been simply copied from:
No words to say - the site is complete spam.
Taking someone else's site, replacing images and text, and registering it as your own is illegal and unethical.
However, spammers lack this moral consideration.
Learn more about cloned sites.
My interest is to investigate more. I remained in contact.


"I own a house in Ca and I also own a house in Texas where I have my private archaeology company …. Private archaeology company is in Texas.."
First picture:
"I live alone with my dog and his name is Terry..."
😏 "One car is for me, and the other car is for my dog." Is it how I should read it?
The second picture is even more interesting.
Using google reverse image search I found the image source:
Historic Name:WILLIAM KELLOGG HOUSE
You would say 'the location markers' were the clues. Yes, you are right.
How audacious must "spammer #1" be to send pictures of random houses from the internet?
Also, do you see a watermark "© Google 2003" on the picture?
Check what kind of tools can provide you with more detailed information about pictures.
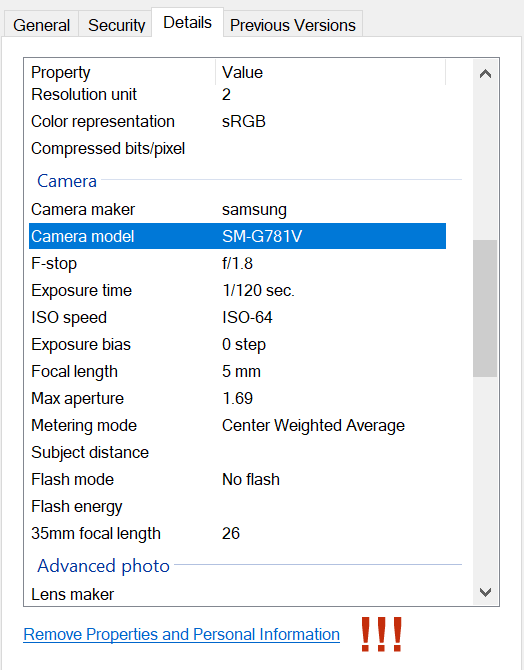
Image metadata, often stored in formats like EXIF and IPTC, can provide a wealth of information about an image.
EXIF Information:
EXIF data typically includes details such as camera settings, date and time the photo was taken, GPS coordinates (if available), camera model, and more.
IPTC Information:
IPTC data is more focused on describing the content of an image. It includes fields for titles, captions, keywords, creator information, copyright details, and more.
Together, EXIF and IPTC info offer a complete view of a digital image, covering both technical and descriptive aspects.
EXIF tags checking for these 2 particular images
First image:
CreateDate - 2023-11-14
Second image:
CreateDate - 2023-11-13
😏 "Spammer #1" took a picture in California on Monday, then the second house in Texas on Tuesday. Both images have an IPTC comments field labeled 'screenshot'.

"… I'm excited to start our chapter. I believe that people meet for a reason, ...[skipped]. You are a wonderful person and your beauty is beyond measures. ......"
As much as I appreciate compliments, I don't trust statements like "your beauty is beyond measure."
Let's pause here and explore why I have doubts about such a lovely message.
Let's go back to the subject
Domain Registered: 2024-03-21
Domain Expires: 2025-03-21
1 year registration
I don't visit suspicious sites directly because I don't want to have to clean my computer afterward. I am using https://validator.schema.org just to see the source.
By checking the source code, I noticed folders for images such as "uploads/2020/10/" marked by dates that don't correspond to the site's registration date.
This is a clue that the "spammer #2" site has been cloned.
Cloned websites refer to replicas or copies of existing websites created with the intent to deceive users or to engage in fraudulent activities.
Read further to find out how to detect that a site has been cloned.
I need to mention that Google is not displaying the "Spammer #2" cloned site in the results.
It's very easy to clone a website these days, as there are plenty of tools available.
Cloned sites can distribute malware, phishing scams, or other cyber threats, posing significant risks to users' online security and privacy.
You can use plagiarism detection tools like Copyscape, Grammarly, or Plagscan to check the website's content is appearing elsewhere.
I didn't take the effort to use the tools. I simply Googled the phrase from the "spammer #2" site.
"Your forest has a significant impact on the health of our environment and planet. When timber from your forest is used for buildings and products, the wood being used has permanently stored CO2 pollutants pulled from the atmosphere."
In one second, I knew that the "spammer #2" site had been cloned from another site.
The "spammer #2" didn't even bother to replace the images of people on the "Our Team" page.
Read more how to protect yourself against the risks associated with cloned websites
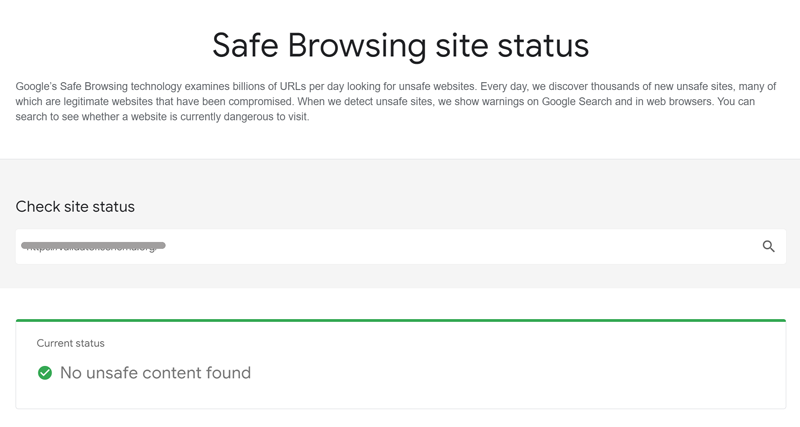
Safe Browsing
1. Ensure your browser and security software are updated with the latest patches.
Google Safe Browsing site status may yield different responses based on various factors such as the type of threat detected, the severity of the threat, the timing of the scan, and the current status of the website. These responses can range from warnings about potential security risks to notifications about recent scans and updates.
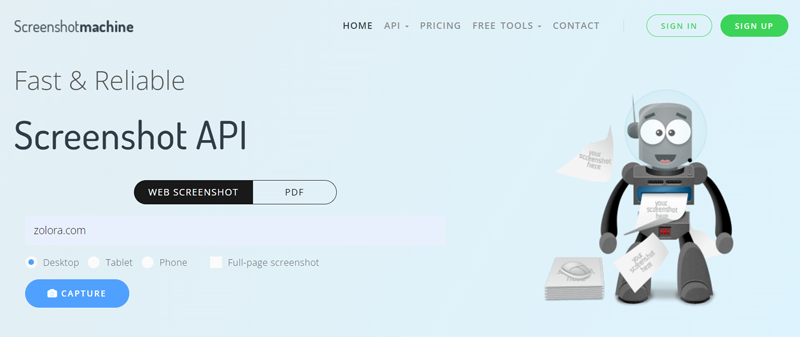
3. If you want to check out a suspicious webpage without actually visiting it, the easiest and safest way is to use an online tool that takes screenshots of websites.
Example: Screenshotmachine
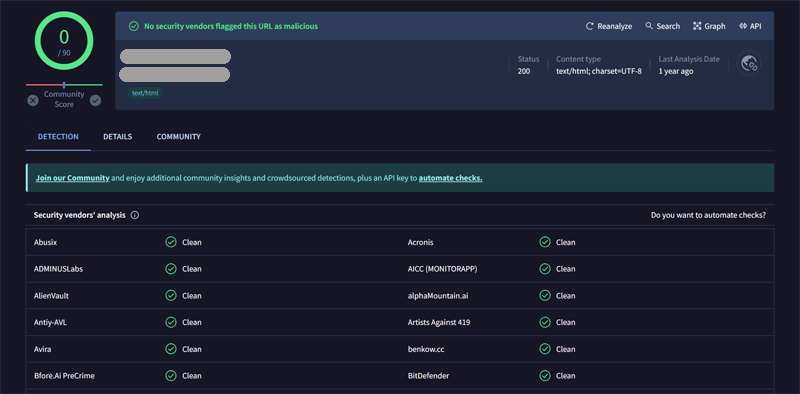
VirusTotal:
5. Without having to visit a site, you can use Schema.org's Validator to view the source code, provided you can read it.
6. You can check the site registration at who.is
Reverse Image/Video Search and Metadata

Here's how to use Google's reverse image search on a computer:
1. Go to images.google.com2. Click the camera icon
3. Drag and drop an image or click Upload an image
4. Click Search
Please note that the Google results for people are limited.
TinEye.com is another way to find images online.
IPTC and EXIF information:
Usually social sites are deleting all this information, but if you received a photo directly - there is a chance you can find a lot of interesting information.
- To view the EXIF data in digital image files on a Windows PC, probably the easiest option is simply to right-click on the image file, select Properties and click the Details tab.
-
Some paint tools have "File Info".
For example, Adobe Photoshop
can read IPTC and EXIF information. - Online tools. I will not reffer to a particular one. You can google "iptc exif online tool" - you will find plenty on tools.
I used three exclamation marks to emphasize the importance of removing properties and personal information from images before sending them to someone you don't know well.
Speaking of your phone camera location settings, have you checked if the location tags are turned off?
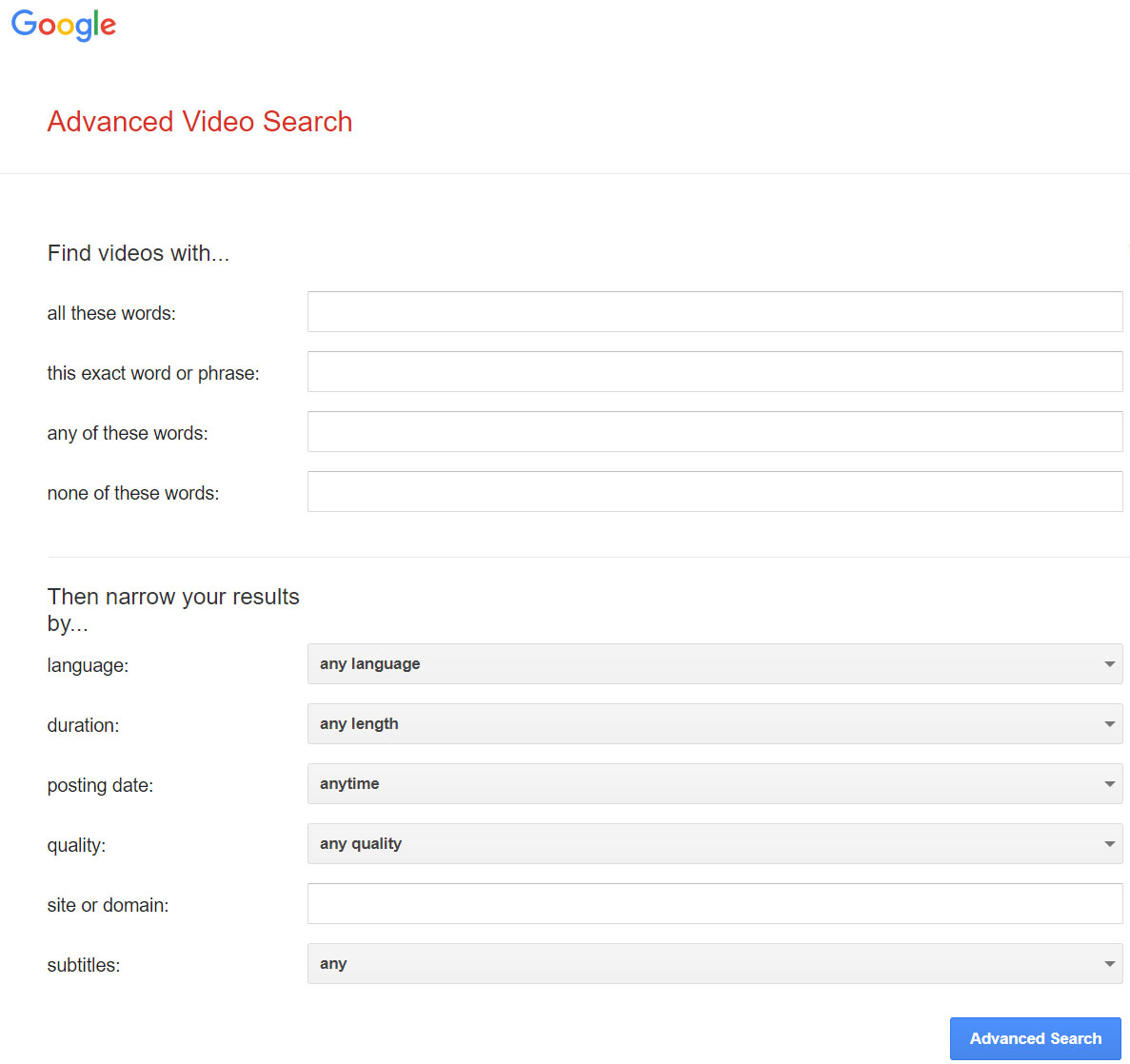
Advanced Video Search by Google
https://www.google.com/advanced_video_search
While it's not overly complex, using Advanced Video Search effectively might require some familiarity with the types of filters available and how to apply them to refine your search results.
While Advanced Video Search may not directly uncover dating spammers, it can assist in identifying warning signs and suspicious behavior that may indicate a dating scam.
Check out my real example of doubting the video source provided by a scammer.
Cloned Websites
Cloned websites can cause significant harm in several ways. They can deceive visitors into divulging sensitive information, such as passwords or financial details, leading to identity theft or financial loss. Additionally, they can create fake but convincing business profiles to build trust and appear genuine.
How to recognize a cloned website?
-
Before starting your research, ensure you're safe when working with links.
Don't forget to use Google Safe Browsing Diagnostic Tool
http://www.google.com/safebrowsing/diagnostic?site=[site url]to run a Safe Browsing Diagnostic for the site. -
If you are 100% sure the site link is safe, you can use "View Page Source" or "Inspect" from the right-click menu to check the HTML source.
Alternatively, you can use Schema.org's Validatorhttps://validator.schema.org/to view the source code without visiting the site directly. Simply enter the URL of the site under investigation there. -
Search for a phrase of 2 or 3 sentences and Google it.
Google will return the original source to you.
Expires On: 2025-10-22

Expires On: 2025-03-21
-
Shortcut: use CopyScape
https://copyscape.com
CopyScape is a free plagiarism checker.
The problem is that Copyscape returned me another copycat (cloned) website as the source.
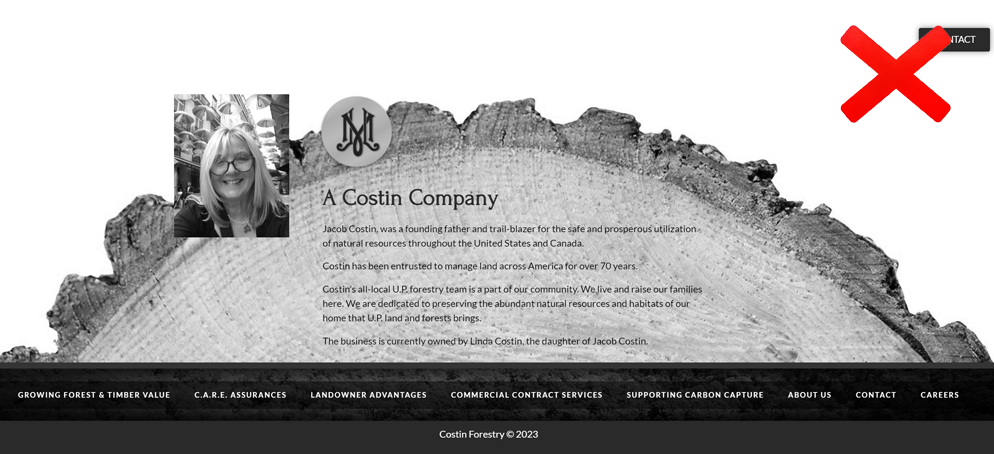
Google has systems in place to detect and address cloned or duplicate content.
When you search for information, Google aims to return the most relevant and authoritative sources.
So, I'll stick with just Googling some sentences.
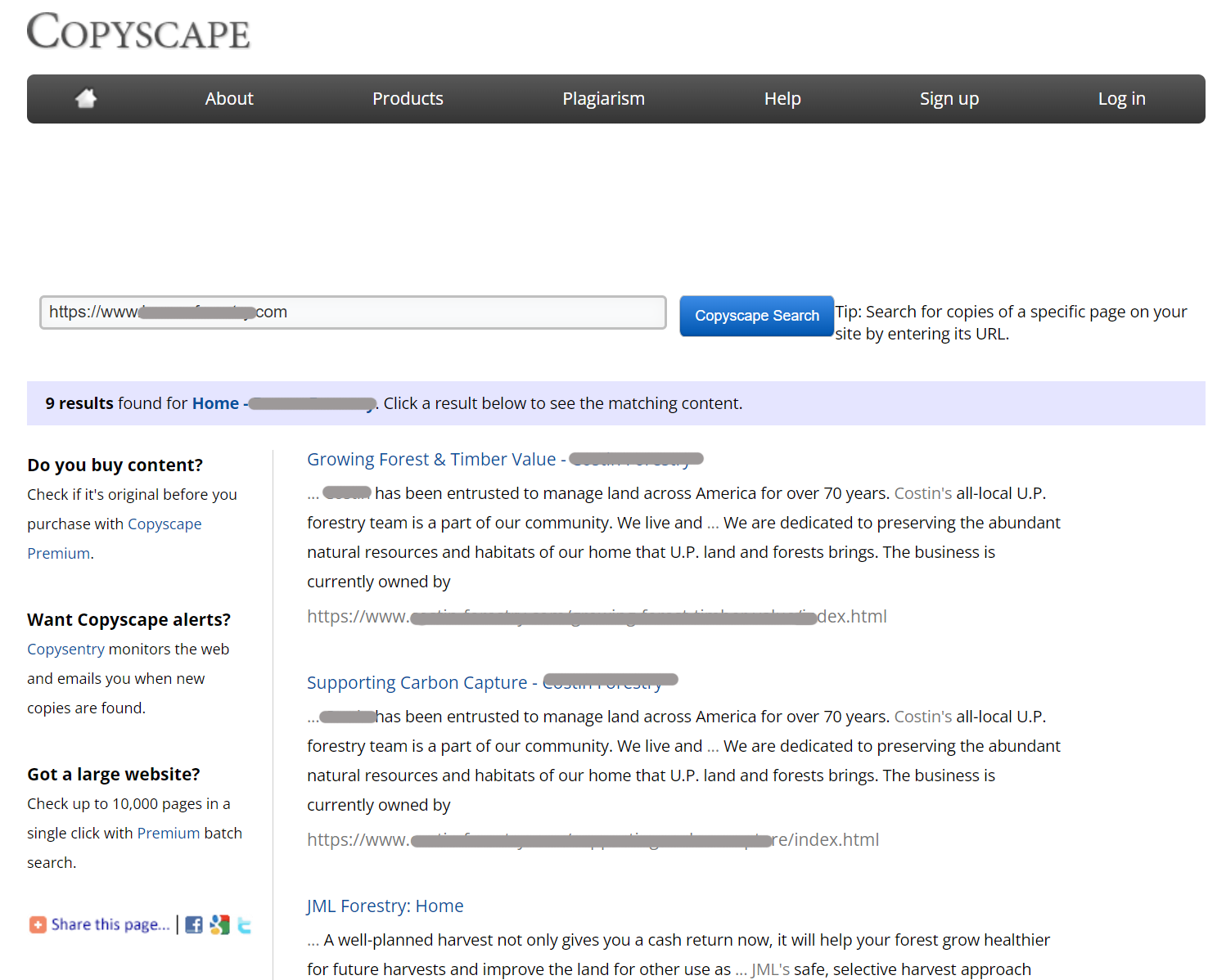
-
Check the registration dates on whois.com.
The original site:
Registered On: 2020-10-22. Registered for 5 years.The first copycat:
Registered On: 2024-03-20. Registered for 1 year.The second copycat:
Registered On: 2023-12-09. Registered for 1 year.
What to Do If You Found the Site is Cloned
-
DMCA Takedown Notice:
File a DMCA takedown notice with the hosting provider of the cloned site. This can result in the site being taken down. -
Search Engine Complaint:
Report the cloned content to search engines like Google to have the duplicate content removed from search results.
Investigations Outcome
"Spammer #1" - I wasn't patient enough to continue. I already discovered that his site has a fake business profile.
To me from the "Spammer #1": "I just want to check up on you... I hope to hear from you soon..."
I'm trying to be polite with everyone, even though I know whom I am dealing with. However, as a web programmer, I dislike it when someone creates fake websites.
There is my answer:
Hello Mike!
Regarding your website:
It's registered only for 1 year starting from August.
The office address listed on the site is in VA, not in TX.
There's only one picture of you, seemingly on a beach in Hawaii.
How are the famous artifacts related to your work?
There are no pictures of your team or past projects.
You mention being "licensed" without a state license.
Are you phishing?
😒 Never heard from the "spammer #1" again.
To me from the "Spammer #2":
Good Morning sweetheart...
[skipped].
I was so exhausted last night, I woke up to the airport company calling me and telling me that they wont be able to get my stuff back, they saw someone on the camera walking out with it, covering his face. There’s nothing they can do.
[skipped the rest]
Dating spammers employ a money scam strategy by crafting emotionally compelling stories, narrating personal struggles and hardships, and then requesting funds for fabricated travel expenses, medical emergencies, or other fictitious needs.
"We arrived safely in Vancouver, Canada. it was a long day. I lost my luggage at the airport, they said they'll try to locate it and keep me informed. My fingers are crossed, I need my laptop for work purposed. The day couldn't get any worse."
The spammer #2 is in trouble, but he already knows I found the source of his cloned "business" site.
He's trying to save the situation by sending photos and videos of his "tree-cutting" activities in Vancouver.
"My workers started with fumigation to eliminate dangerous insects and spiders."
And a video attachment has been sent to prove the activity.
It wasn't easy, but I found the source of the video using Advanced Video Search by Google
https://www.google.com/advanced_video_search
https://www.dailymail.co.uk/video/news/video-1339172/A-futuristic-looking-machine-cuts-strips-trees-seconds.html
The original video: By Francis Scott For Mailonline
Smart machine to cut trees. Ripped out of the ground and stripped for firewood in seconds: Watch the giant robotic arm that saws through the forest and cuts up a tree trunk in seconds
Date: 12 Oct 2016.
Nothing about money has been asked yet, but I didn't want to listen to a sob story or be asked for help.
So, I simply sent the link to the original video.
😒 Never heard from the "spammer #2" again.
The Bottom Line is...
I asked ChatGPT about common strategies employed by dating spammers. Here are some tactics they use, along with my comments.
-
Fake Profiles:
-
Attractive Photos: Use stolen or stock photos of attractive individuals to lure victims.
I believe that Spammer #1 and Spammer #2 were sharing their own photos as well as photos of their pets. Therefore, I wouldn't fully agree with the ChatGPT's statement.
-
Compelling Bios: Create fake but convincing bios to build trust and appear genuine.
Dating site scammers may claim to travel a lot.
They need excuses for why they can't meet in person or why their communication may be sporadic.
Scammers often use their supposed travels as a pretext for requesting money from their targets. They may claim to encounter unexpected expenses or emergencies while abroad, exploiting the sympathy and generosity of their victims.
😃 Spammer #1 purported to be a licensed architect based in Texas, claiming to operate a private firm with global reach. Despite stating a local base, the firm allegedly extended its services across continents, including North America, South America, Europe, Asia, and Africa!
😃 Spammer #2 got a contract in Vancouver, Canada on the third day of our communication. The following day, he purportedly encountered troubles at the airport.
-
Attractive Photos: Use stolen or stock photos of attractive individuals to lure victims.
-
Love Bombing:
- Intense Affection: Quickly express strong feelings of love or affection to make the victim feel special and emotionally attached.
- Frequent Contact: Maintain constant communication through messages, calls, or emails to build a sense of intimacy and trust.
Expressing love quickly on dating sites is a calculated strategy employed by scammers to exploit the emotions of their targets and further their fraudulent schemes.
"Scammer #2" wanted to introduce me to his sister on the third day of our communication. I suspect that the "sister" was actually a team member or accomplice in the scam.
Avoiding emotional connection with spammers on dating sites requires a combination of vigilance, skepticism, and awareness of common tactics used by scammers.
- Stay skeptical, be cautious of individuals who profess strong feelings of love or affection very early in the conversation.
- Verify information and don't be afraid to ask specific questions about their background or experiences
- Avoid sharing personal information
- Don't dismiss your gut feelings in favor of the emotions
- Take the time to get to know the person gradually
- Be wary of sob stories
-
Sob Stories:
- Personal Tragedies: Share fabricated stories of personal hardship or emergencies to elicit sympathy.
- Financial Needs: Claim they need financial help due to these emergencies, prompting the victim to send money.
I didn't have a chance to listen to any sob stories. I ended the correspondence too early; it was getting boring to continue.
But "Scammer #2" seemed so close. He claimed to have lost his belongings at the airport, and the airport authorities were unable to retrieve them.
-
Phishing and Malware:
-
Suspicious Links: Send links that lead to phishing websites designed to steal personal information or install malware on the victim’s device.
Utilize the power of reverse image search
Verify if the website has been cloned
- If you suspect an online relationship is a scam, stop all contact immediately.
- If you have already realized that you are a victim of a romance scam, file a complaint with the FBI's Internet Crime Complaint Center (IC3).
- Help stop scammers by reporting suspicious profiles or messages to the dating app or social media platform. Then, tell the FTC at ReportFraud.ftc.gov
Additional Resources to Report Suspicious Activity
-
Suspicious Links: Send links that lead to phishing websites designed to steal personal information or install malware on the victim’s device.

To protect yourself from dating spammers:
- Verify Profiles: Conduct reverse image searches and look for inconsistencies in the person’s story.
- Be Cautious with Personal Information: Avoid sharing sensitive information with someone you’ve just met online.
- Recognize Red Flags: Be wary of anyone who professes love quickly, asks for money, or shares inconsistent stories.
- Report Suspicious Activity: Use the platform’s reporting tools to flag suspicious profiles and activity.
- Use Secure Platforms: Stick to reputable dating platforms that have measures in place to detect and prevent fraud.
Share Your Story
Could you please share your experience or any story you've heard about romance scammers?
- Have you or anyone you know ever encountered a romance scam?
- If so, how did you or they realize it was a scam?
- What were some warning signs that stood out?
- What steps did they take to recover from the scam and protect themselves in the future?
- How did the scammer react when questioned about their intentions or authenticity?
- What specific behaviors or messages did you or they find suspicious?
- Were there inconsistencies in the scammer's stories or details about their background?
- Were there requests for money or financial assistance, especially for emergencies or unexpected expenses?

Learning from real-life stories can help raise awareness and prevent others from falling victim to similar scams.
Understanding the warning signs can help others stay vigilant and protect themselves from falling victim to similar scams.
